
How to Prevent Cyber Attacks on Businesses
Protect your growing business from current cyber security threats and potential attacks.
For many businesses, cybersecurity was long an afterthought—a problem for the IT team. However, in recent years cybercrime has exploded in volume, sophistication and impact, forcing organizations to make security a priority or suffer the consequences. The average cost of a data breach for U.S. businesses is now $9.44 million—more than twice the global average, according to IBM Security. That number does not include the effect on employee productivity, the company’s reputation or potential lost profits.
The cybersecurity problem increased during the rapid shift to remote and hybrid work environments, which introduced digital infrastructure with a myriad of potential access points for cybercriminals to infiltrate. By using stolen credentials or social engineering trickery, threat actors are often able to compromise security without having advanced technical abilities. Criminals can exploit both vulnerabilities in software and human behavior to hack web applications, export data, launch ransomware attacks and more, not only in your company but in vendors who have access to your systems.
To help your organization manage and prioritize its cybersecurity needs against today’s threat landscape, Fifth Third Bank is presenting a series of articles designed to alert businesses to the latest cyberthreats and provide a detailed guide on how to help protect against them. While the task may seem daunting, the good news is that a strong security foundation can be built even on a limited budget. Arming yourself and your staff with security knowledge is an excellent start.
Common Cyber Threats Against Businesses
Cybercriminals use a variety of threats to launch attacks against businesses. Often, data breaches happen over a series of security events, making detection that much more difficult. However, if you trace security incidents or breaches back to their root cause, you discover that cybercriminals still heavily rely on a few tried-and-true tactics to gain initial access to business networks.
The most common methods involve manipulation of human behavior and emotion through social engineering. Cybercriminals rely on human fallibility for their attacks to work, whether by exploiting behaviors or capitalizing on human error. In fact, 82% of breaches involve the human element, according to the 2022 Verizon Data Breach Investigations Report (DBIR). Despite being one of the oldest cybercriminal techniques, phishing—fraudulent emails that trick users into handing over sensitive information—is still one of the top ways threat actors infiltrate businesses. Phishing is behind nearly 20% of breaches.
But phishing is a means to an end, not always the way in. What criminals phish for are credentials, such as employee login information. In fact, credential theft is the leading root cause of data breaches. It’s also the leading result, with cybercriminals stealing additional credentials for their own use or to sell on the black market. Rounding out the top social engineering methods is business email compromise (BEC), which involves threat actors impersonating employees through compromised email accounts.
Additionally, cybercriminals access business networks via exploited vulnerabilities, especially those that are the result of misconfigured cloud components. Whether through phishing, BEC or the use of desktop-sharing software, ransomware attacks are increasingly common against organizations, especially those that not only freeze systems and files but threaten extortion unless a hefty ransom is paid.
See infographic transcript below
Common Cyber Security Threats
1. Phishing
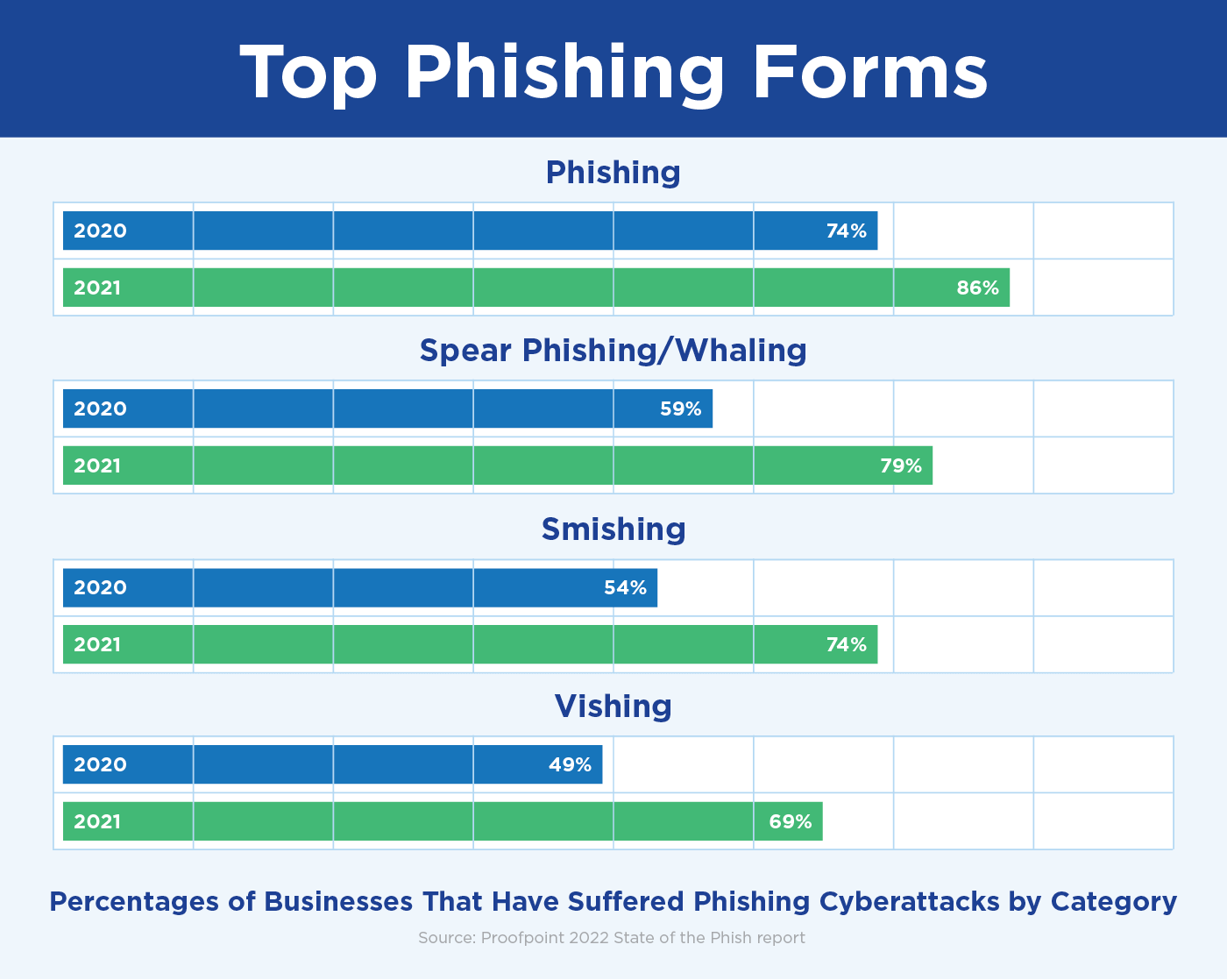
While phishing might be one of the oldest cybercriminal activities, phishing techniques have evolved a great deal over the last couple decades. Bulk, indiscriminate phishing attacks rose by 12% year over year targeting 86% of organizations, according to Proofpoint’s 2022 State of the Phish Report.
Growing at a faster rate, however, are phishing campaigns that target specific employees or executives, known as spear phishing and whaling, which increased by 20% to 79% of organizations. Reports of smishing, or SMS/text message phishing rose 21%, and vishing, or phishing by voice call, increased by 27%, targeting 74% and 69% of businesses, respectively.
One of the most popular and successful phishing methods against businesses is to send fraudulent emails posing as a vendor, partner or service used by the organization. Pretending to be one of those accounts needing updated profile information can trick staff members into entering their credentials into a malicious website. In fact, Proofpoint found that 30% of working adults think that emails with familiar logos are safe, but those logos can be easily spoofed by phishing scammers.
Phishing campaigns can do more than collect credentials, however. Employees that open attachments or click on embedded links could be inadvertently launching malicious software or malware, such as downloaders that install on systems and wait for instructions or worms that spread laterally before dropping ransomware on servers and endpoints. Nearly 15 million phishing messages with malware payloads were directly linked to later-stage ransomware in the first three quarters of 2021 alone.
2. Business Email Compromise (BEC)
About 77% of organizations faced BEC attacks in 2021, an 18% increase over the previous year, according to Proofpoint research. BEC is a major threat vector for cybercriminals because employees use email as a main communication method and are trained to trust messages from their coworkers—especially their superiors. However, falling for a BEC scam is the second-most costly initial threat vector with a global average of $4.89 million.
In a BEC scenario, criminals send an email that appears to come from a known source making a legitimate request, such as a CEO asking her assistant to purchase dozens of gift cards as employee rewards or a vendor sending an urgent invoice with an updated mailing address. When cybercriminals are able to compromise or copy a business email account, a process known as spoofing, they can easily dupe employees into committing fraud without realizing their mistake.
3. Credential Theft
Credential theft was the leading cause of data breach in 2021, when nearly 50% of breaches were the result of stolen credentials, according to the 2022 DBIR. Stolen or compromised credentials were not only the most common cause of a breach, but at 327 days, took the longest time to identify. In addition, it is one of the most expensive cyberthreats to rectify, costing an average of $4.5 million globally.
Credentials can be obtained by cybercriminals in a number of ways, from phishing emails to sales on the black market—even simply found in unsecured, cloud-facing databases. In addition, threat actors steal credentials from organizations in data breaches, either to access web applications and privileged accounts or to sell to the highest bidder. As our reliance on internet-facing software grows, so too will cybercriminal attempts to abuse our digital identities for profit.
4. Ransomware
According to the 2022 Verizon DBIR, ransomware increased by 13% from 2020 to 2021—a jump as large as the previous five years combined. In addition to volume and frequency, ransomware attacks have also increased in complexity and impact. Threat actors rarely settle for a negotiated insurance payout; instead, their ransom demands have risen by 45% to an average of $247,000 according to Help Net Security.
Ransomware attacks against businesses today are rarely solo events. Instead, cybercriminals typically gain access to networks through desktop-sharing software, unauthorized use of credentials, malware dropped in phishing emails or exploited vulnerabilities. They then deploy ransomware to monetize their access. However, locking systems and encrypting files is no longer where a ransomware attack ends. Most now include threats of extortion, with criminals publishing sensitive data on public-facing websites unless more money is delivered.
5. Exploited Vulnerabilities
About 7% of breaches were caused by exploited vulnerabilities, double the amount from the previous year, according to the 2022 Verizon DBIR. Some of these are the result of not updating software and operating systems, as well as zero-day exploits, which are vulnerabilities that are discovered by enterprising cybercriminals before patches can be created and deployed. However, the majority of breaches in this category are because of misconfigured cloud storage.
IT staff may misconfigure cloud components—firewalls, APIs, cloud email servers and web applications—creating vulnerabilities that serve as network on-ramps for bad actors. Misconfigured cloud buckets in particular were responsible for about 40% of employee errors that led to compromise in 2021. If buckets are created without proper access control lists (ACLs) defining who has access and at what level, they can "leak" data onto the open internet. And because buckets often house sensitive information, this data can later be used for attack.
How to Protect Your Business from Cyber Attacks
For a long time, it was enough for businesses to purchase technology, such as firewalls and antivirus protection to stop most cyberattacks. However, today we all need to do more. While technology can thwart many cyberthreats, the most important factor in mounting a full defense of your organization is the security awareness of its people. By teaching employees how to identify and avoid digital threats, you can change the human behavior cybercriminals rely on for their schemes to work. By implementing smart processes and technologies, you can protect the health of your systems, too.
Here are a few steps your organization can take to protect against the top cyberthreats today:
Protect with Security Awareness
Cyberthreats: Social engineering, phishing/smishing/vishing, BEC
- Train employees to review all communications with skepticism, including those from coworkers. Be aware of the following:
- Urgent language requiring action immediately
- Strange payment requests outside of normal processes
- Requests to update profile information via hyperlink
- Emails from unknown senders with attachments
- Conduct regular phishing tests and collect metrics to determine if the training is working.
- Offer seminars on the latest cyberthreats and tips to avoid them each quarter.
Protect through Process
Cyberthreats: Exploited vulnerabilities, credential theft
- Immediately update all operating systems and software when updates are released.
- Set updates to automatic, if available.
- Configure cloud buckets to "private" and include ACLs to determine access privileges.
- Implement strong password requirements, including at least 10 characters with numbers, symbols and upper- and lower-case letters.
Protect with Technology
Cyberthreats: Credential theft, ransomware
- Consider using a single sign-on service (SSO) for all web applications that is protected with multi factor authentication (MFA). MFA adds an extra layer of security by requiring two or more forms of verification to access platforms, including:
- Something the user knows, such as a username or password
- Something the user has, such as a security token or a cell phone
- Something the user is, such as a fingerprint or face ID
- Layer security software with anti-malware and anti-ransomware programs that can detect, respond to and remediate cyberthreats.
- Implement automatic backups that are stored in a secure cloud platform or on a server segmented from others.
Cybersecurity is no longer just a problem for the IT helpdesk. All employees, partners and third parties of an organization need to be vigilant to protect against today’s threats. The cybersecurity expertise provided here and in future articles in this series will help you gain the skills to protect customer and proprietary data, devices, networks and even the health and finances of your business. By increasing your security awareness, you make your organization and its digital infrastructure a safer place for all employees.