
Protect Your Business From Email Scams
How to guard against “phishing” tricks and malicious software to keep your business email safe.
Business email compromise, or BEC, may sound benign compared with other cyberthreats like ransomware or brute-force attacks. But BEC incidents cost businesses billions of dollars a year and bear far greater financial losses than ransomware, according to the FBI.
BEC is an email-based scam that typically targets high-ranking business executives within companies of all sizes, but especially small and mid-size businesses. Threat actors will often use spoofed or compromised email accounts of these executives to dupe employees of the targeted organization into transferring payments for illegitimate invoices or services to accounts controlled by criminals.
The threat actors use social engineering tactics such as phishing to trick their targets into providing their email credentials or installing malicious software to gain access to an executive’s email account. Masquerading as that business leader, threat actors may email a finance employee claiming that an urgent circumstance requires an immediate wire transfer. Because the request appears to be from a trusted company executive, the finance employee may unquestioningly submit the payment, which flows into the fraudster’s bank account.
BEC crime is not limited to fraudulent payments. Sometimes the attack aims to fabricate inside information for use in subsequent BEC attempts. To that end, criminals may ask for an individual’s login credentials or contact human resources to glean personal and corporate data such as wage and tax statements.
Regardless of intent, the sheer amount of information that can be gained through social engineering and email account takeovers can lend a great deal of support to these scams. The seemingly genuine emails appear to be from a known executive or vendor, a tactic known as email spoofing. Similarly, the bogus websites to which criminals link look genuine, which is a tactic known as domain spoofing.
BEC isn’t new; it’s been around for a decade. Yet the crime has not gained the notoriety of other cyber threats. One reason for this is that business victims rarely report BEC to avoid corporate embarrassment. The numbers, however, tell an unambiguous story. According to the FBI’s Internet Crime Report, BEC caused global financial losses of almost $2.4 billion in 2021, a 28% increase over 2020. In fact, financial losses attributed to BEC in 2021 were 49 times greater than those caused by ransomware, according to the FBI.
"Ransomware tends to be a more high-profile crime because it can be extremely impactful to operations and can disrupt supply chains, public entities like school districts, and even the power grid," says Tom Scarborough, Senior Vice President and Senior Director, Extended Security Programs, at Fifth Third Bank. "BEC, in comparison, is much less visible. But it’s a substantially more costly crime."
How BEC Became a Bigger Threat
The surge in BEC incidents can be attributed to a great extent to the COVID-19 pandemic. The rapid shift to remote work, for example, has expanded the use of email and virtual communications tools. Cyber criminals quickly targeted employees working from home, who may lack the on-site cybersecurity and supervision offered at the physical workplace. In a new twist, the FBI says criminals are manipulating remote-work and virtual communications tools to invite workers to phony digital meetings and convince them to transfer funds to illicit accounts.
BEC incidents can be hard to detect because of the social engineering being used by bad actors to trick employees, but they are preventable. Phishing emails, for example, can be identified with security awareness programs. Using technology, firms can root out phishing emails that have embedded malware and defuse the threat.
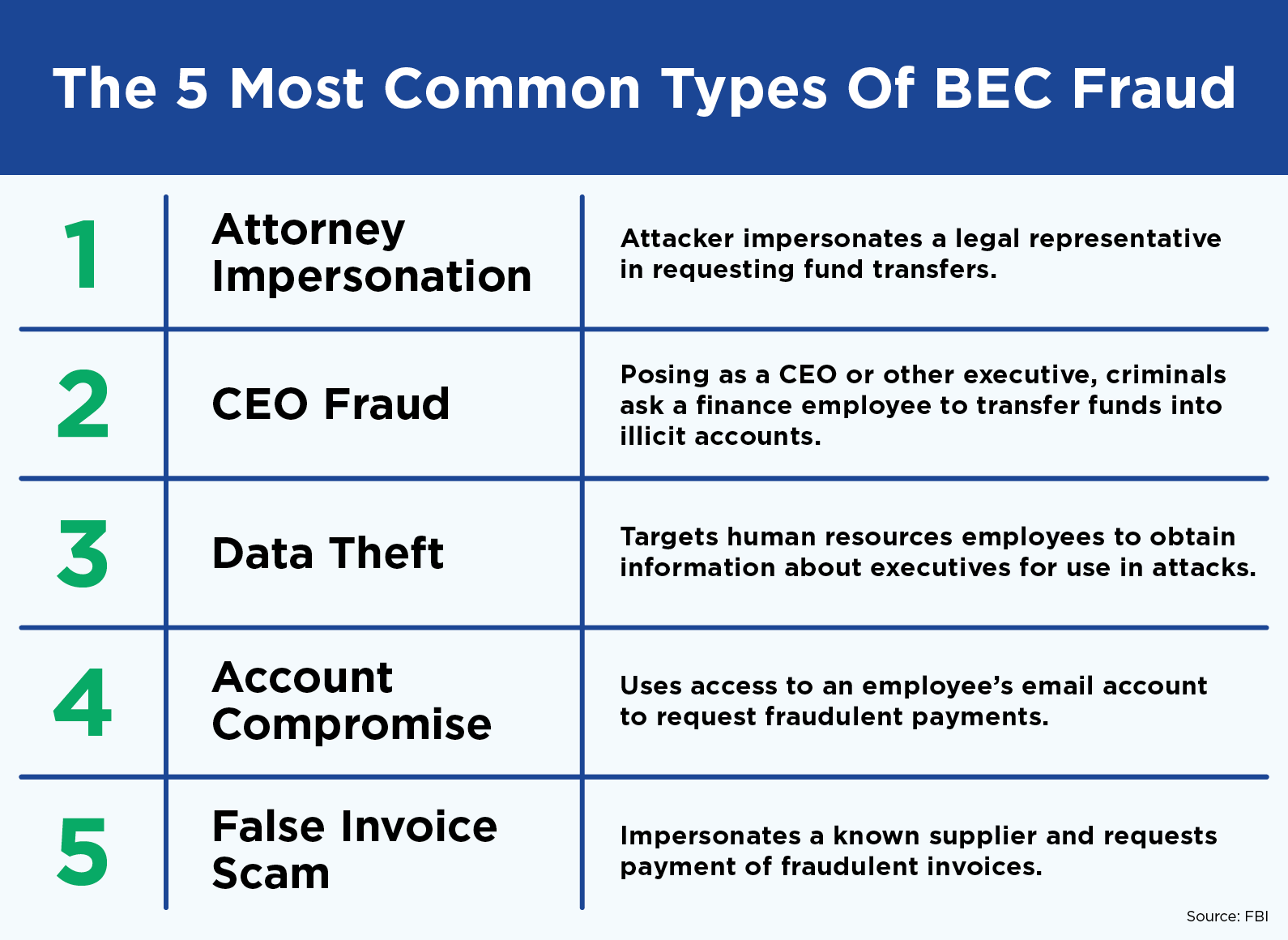
The Main BEC Threats to Guard Against
There are three main approaches that criminals use to compromise business email:
- Spoofing an email of an employee—creating a message with a fake address—is very common, but the least sophisticated.
- More sophisticated attacks will create an email that is very similar to a real business address in hopes of tricking unsuspecting colleagues.
- Finally, bad actors will use either phishing strategies or malware to take over an executive’s actual email account and issue payment instructions.
Typically, criminals may start by identifying a top executive or employee with access to company finances, payroll data, and other sensitive information. Next, they launch a confidence campaign by altering an individual’s email address or a company website URL in almost imperceptible ways. They are betting that inattentive workers will be unlikely to notice the difference between a legitimate address, such as [email protected], and a slightly doctored address like [email protected].
Using these system credentials, threat actors send authentic-looking emails calculated to hoodwink recipients into disclosing confidential information such as login credentials or account information. Doing so can enable threat actors to glean inside information from corporate email discussions, account activity, and data to build background information needed to carry out a credible scam. Inside knowledge of company billing and invoicing activity, for example, enables scammers to create invoices and payment requests that appear to be from a known supplier but bear a different payment account number. Alternatively, criminals may implant malicious software, or malware, on the company’s computer systems to gain access to its networks, email accounts, and financial data.
How to Identify Potential Email Scams
Keep these telling signs in mind to sort through potential email scammers:
- lightly misspelled email and URL addresses.
- Awkward language and punctuation.
- Incorrect payment account numbers.
A sense of urgency: The sender is pressing you to act quickly.
- Executives claiming to be on vacation or traveling for business.
- The requester is not available for a phone call, only email.
- Use of email rules to forward messages to hidden folders.
- Use of fake email chains using subject lines with "Re:" or "Fwd:"
Best Practices to Avoid BEC Attempts
"Given the nature of BEC, it can be hard to prevent and detect," Scarborough says. "One of the best defenses is a robust security awareness and education plan. Make sure your employees, especially those in money moving roles, are aware of these types of threats and I strongly encourage the use of phishing exercises so they see what these threats ‘look and feel like.’ It is a low cost, low tech, but very effective best practice."
Here are some other best practices to utilize to prevent BEC:
- Educate company executives and employees on BEC threats, email security best practices, and basic cybersecurity hygiene.
- Verify email addresses and URL hyperlinks to ensure they are correct.
- Never provide login credentials or personal information via email.
- Limit personal and professional information shared online or on social media.
- Think before clicking hyperlinks and attachments in email.
- Minimize the number of individuals with authority to approve or perform wire transfers or ACH payments.
- Implement policies for separation of duties and/or dual-approval processes.
- Never accept payment requests via email or other digital channels.
If You Fall Victim to a BEC Scam
Immediately contact the financial institution holding the compromised account, report the crime to your local FBI field office, and file a complaint with the FBI’s Internet Crime Complaint Center (IC3).
If you would like more information about protecting against BEC scams, please contact your Fifth Third Bank Treasury Management Officer, Relationship Manager, or .